Antivirus (AV) software will help protect a computer from hackers.
a. true
b. false
Ans: b. false
You might also like to view...
The ____________ is a post test loop, which means it performs an iteration before testing its Boolean expression.
a. for loop b. while loop c. do-while loop d. do-before loop
Public-key algorithms are based on __________ .
A. permutation B. mathematical functions C. substitution D. symmetry
If two tables do not have a common field, Access will join the two tables by combining the records, regardless of whether they have a matching field. This is known as the multiplier effect
Indicate whether the statement is true or false
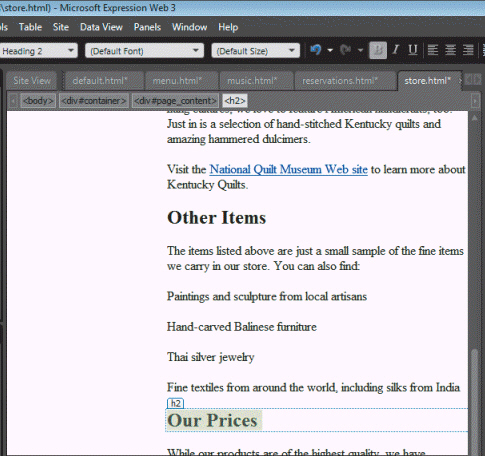 Referring to the figure above, if you wanted to change Heading 2 to Heading 1, you would select the ____.
Referring to the figure above, if you wanted to change Heading 2 to Heading 1, you would select the ____.
A. Selector list arrow B. Selector list box C. Style list arrow D. Style list box