When qualifying an incident as a computer crime, which of the following characteristics would not be considered a valid description?
a. The data in the computer are the objects of the act.
b. The computer is the instrument or the tool of the act.
c. The computer is one of the objects stolen during a burglary.
d. The computer is the target of an act.
c. The computer is one of the objects stolen during a burglary.
You might also like to view...
You can set a motion tween to ease ____.
a. up b. in c. out d. down
Broadband ISDN services will most likely be deployed
a. using only copper cabling b. using only fiber optic cabling c. using copper cabling for long distances and fiber optic cabling for a short distance d. using fiber optic cabling for long distances and copper cabling for a short distance
________ adds depth to a chart
Fill in the blank(s) with correct word
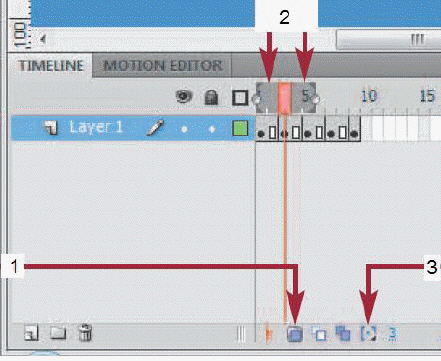 The item marked 1 in the accompanying figure is used to ____.
The item marked 1 in the accompanying figure is used to ____.
A. toggle onion skinning on and off B. decrease the number of frames displayed on the Stage C. increase the number of frames displayed on the Stage D. both b. and c.