Holly is trying to use Windows Defender to run an antivirus scan. Windows Defender refuses to run. She notices a problem when she tries to update Windows Defender and it fails. When Holly opens the Action Center she sees this screen.
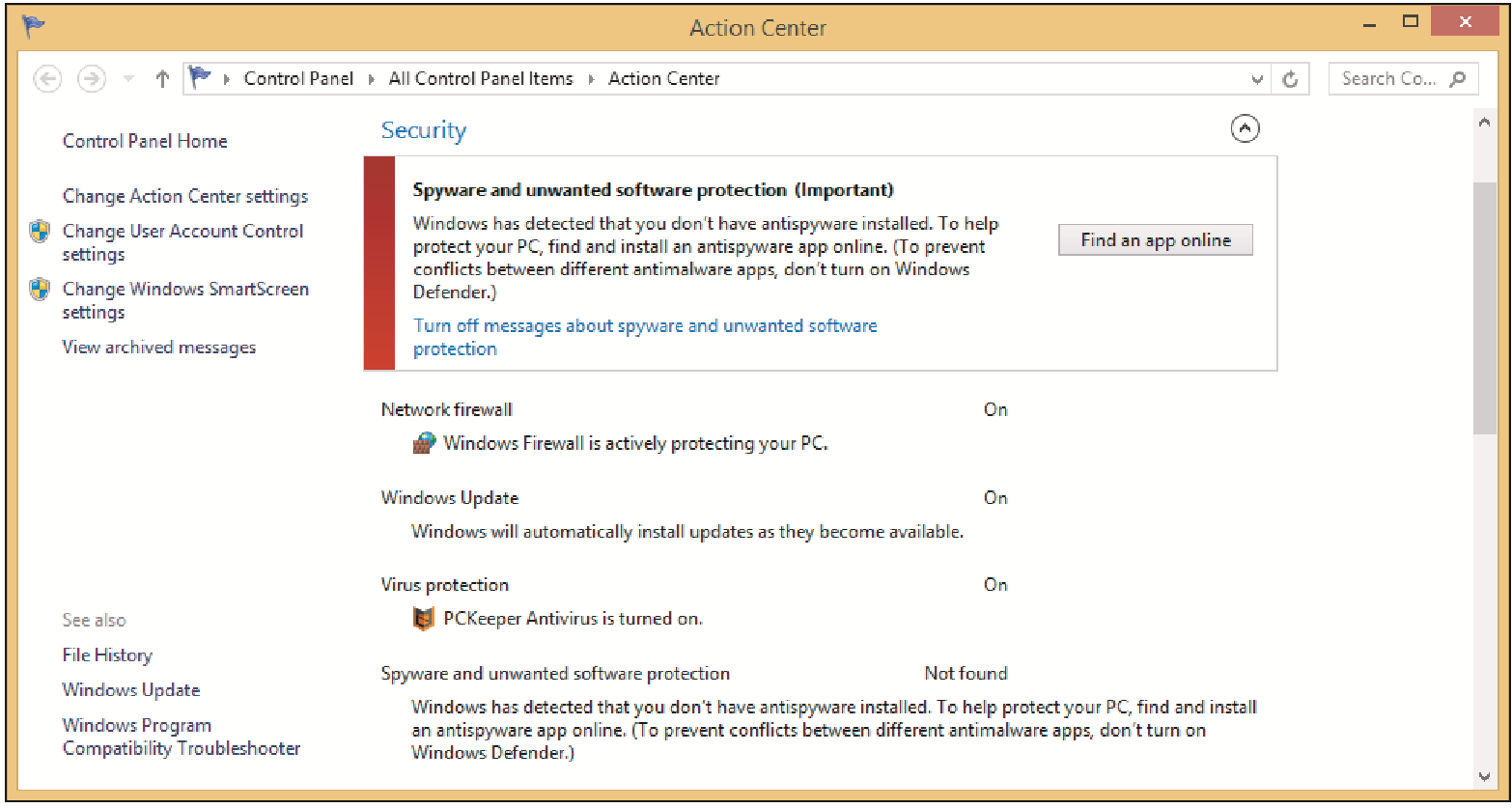
What has happened to Holly’s computer?
A. She has received a spam message.
B. She has received a security alert message.
C. Someone has hijacked her email.
D. She has downloaded a rogue antivirus.
Answer: D
You might also like to view...
Interface Collection contains __________ operations (i.e., operations performed on the entire collection).
a. aggregate. b. composite. c. integral. d. bulk.
Detailed data flow diagrams may be developed by:
What will be an ideal response?
The icon labeled 2 in the accompanying figure represents the ____ command.
a. Layer, Align, Top Edges b. Layer, Align, Vertical Centers c. Layer, Align, Left Edges d. Layer, Align, Right Edges
When using Internet Explorer 11, how do you open a new tab?
A) click the left arrow button B) click the plus sign C) click the star D) click the ellipsis (...)