The original wireless encryption was called ____________________ because it was designed to provide a level of confidentiality similar to that of a wired network.
Fill in the blank(s) with the appropriate word(s).
Wired Equivalent Privacy
Computer Science & Information Technology
You might also like to view...
Which data cable uses four or six pins and is commonly used for connecting portable devices, such as camcorders?
A. eSATA B. USB C. IEEE 1394 D. FireCable
Computer Science & Information Technology
Give five types of delay along with an explanation of each.
What will be an ideal response?
Computer Science & Information Technology
To display a format of 12/30/2018 in a date field regardless of how the data was entered, use the ________ format
A) Long Date B) Date/Time C) End Date D) Short Date
Computer Science & Information Technology
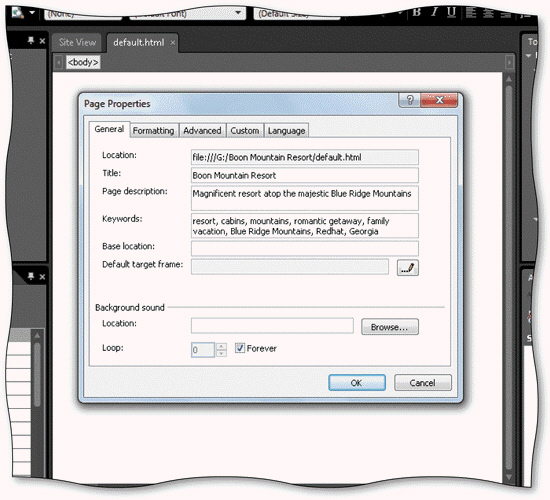 A Web page's title is added on the _____________________ tab in the Page Properties dialog box, as shown in the accompanying figure.
A Web page's title is added on the _____________________ tab in the Page Properties dialog box, as shown in the accompanying figure.
Fill in the blank(s) with the appropriate word(s).
Computer Science & Information Technology