____________________ assurance is the other side of the security assurance coin.
Fill in the blank(s) with the appropriate word(s).
Process
You might also like to view...
Which of the following statements is true of the E-Government Act of 2002?
A. It renews the U.S. government's authority to monitor electronic communications of foreigners abroad and authorizes foreign surveillance programs by the National Security Agency (NSA). B. It requires federal agencies to post machine-readable privacy policies on their Web sites and to perform privacy impact assessments on all new collections of data of ten or more people. C. It restricts government access to certain records held by financial institutions. D. It defines procedures to request judicial authorization for electronic surveillance of persons engaged in espionage against the United States on behalf of a foreign power.
In a database, data is stored in a ________
A) table B) report C) form D) query
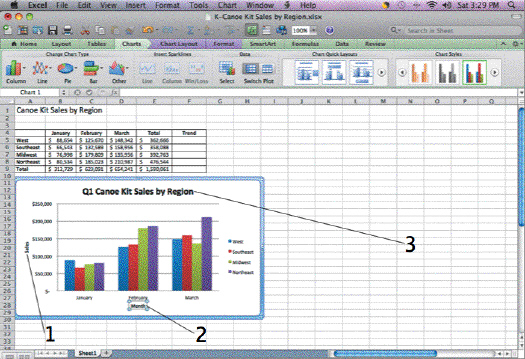 In the accompanying figure, Item 1 points to the ____.
In the accompanying figure, Item 1 points to the ____.
A. horizontal axis title B. vertical axis title C. chart title D. legend
Data can be stored in a text file through the use of ________
A) PowerPivot B) Power View C) HTML D) XML