The most common kind of pretexting in cyberspace is ________.
Fill in the blank(s) with the appropriate word(s).
phishing
You might also like to view...
Provide steps on how to Use Wireshark to Capture and Analyze Ethernet Frames
You will use Wireshark to capture local and remote Ethernet frames. You will then examine the information that is contained in the frame header fields.
Roger purchased a new laptop computer and wants to connect it to a second monitor. The monitor has a DVI and HDMI connection on the back, but his laptop only has a Mini DisplayPort connection. ? Which cable should Roger purchase?
A.
B.
C.
D.
Referring to the figure below, please identify the letter of the choice that best matches the numbered area on the screen.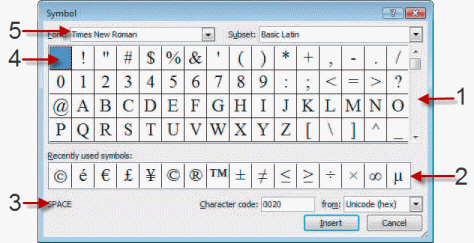
A. Scroll bar B. Recently used symbols C. Name of currently selected symbol D. Currently selected symbol E. Font list box
Your boss created a slide show presentation for an upcoming board of directors meeting. The presentation currently is just plain text on a white background, so she asks you to look at it in a variety of different views in order to determine how to improve it for the meeting. You are looking for a view that shows the slide text in the left pane and not the thumbnails. Which view will work for this? a.Outlinec.Slide Showb.Slide Sorterd.Reading
What will be an ideal response?



