Repeat part (a) by treating each customer ID as a market basket. Each item should be treated as a binary variable (1 if an item appears in at least one transaction bought by the customer, and 0 otherwise.)
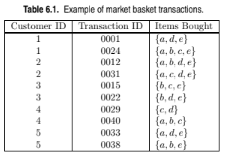
Consider the data set shown in Table 6.1.
You might also like to view...
The Relational and CODASYL models are examples of two different approaches by which a Database Management System will be classified. Make a detailed comparison of each of these models, indicating clearly the relative advantages and disadvantages of each.
What will be an ideal response?
The _______ task must be completed before the Sense Keys task can be completed.
Fill in the blank(s) with the appropriate word(s).
Comcast, Cox, and Charter are examples of local and national ____________________ companies.
Fill in the blank(s) with the appropriate word(s).
____ effectively prevents collisions because every device must wait until it receives permission before it can transmit.
A. CSMA/CD B. CSMA/CA C. Polling D. Fragmentation