Which of the following is used in conjunction with an algorithm to make computer data secure from anybody except the intended recipient of the data?
A. key
B. plaintext
C. cipher
D. cryptosystem
Answer: A
You might also like to view...
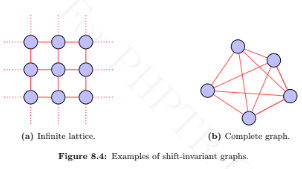
If we can label the nodes in a graph such that the Laplacian matrix of the graph is circulant, then such a graph is known as a shift invariant graph [16]. The eigenvectors of the Laplacian matrix of a shift invariant graph are the same as the columns of the DFT matrix. One example of a shift invariant graph is the ring graph. Draw two more shift invariant graphs and verify that the eigenvectors of the corresponding Laplacian matrices are the same as the columns of the DFT matrix. Also comment on the eigenvalues of the Laplacians of the shift invariant graphs.
You can move to the next field in a form by pressing Enter or Tab
Indicate whether the statement is true or false
How many root keys are in the Registry?
A. Seven B. Four C. Six D. Five
FIGURE AC 1-1 You would open the dialog box shown in the accompanying figure to ____.
You would open the dialog box shown in the accompanying figure to ____.
A. use user templates B. use Quick Start C. compact & repair a database D. use a blank form