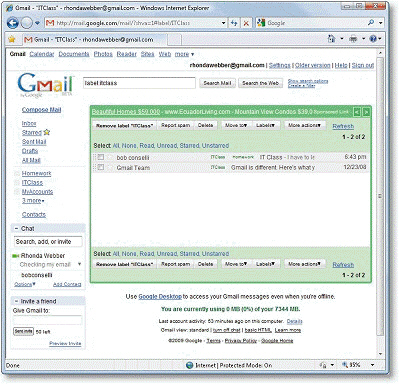
 In the accompanying figure, two messages displayed under one ____________________.
In the accompanying figure, two messages displayed under one ____________________.
Fill in the blank(s) with the appropriate word(s).
label
Computer Science & Information Technology
You might also like to view...
A key characteristic of viruses is their ability _____.
A. to see the contents of your screen B. to perform one function while actually doing something else C. to spread themselves from one computer to another D. to replicate themselves on the host computer
Computer Science & Information Technology
Identify what is contained in the “Network Connection Status” window.
What will be an ideal response?
Computer Science & Information Technology
Find the value of x that makes these equations true.
5-2.6 x+ 2 =4
Computer Science & Information Technology
When a site like Google Docs becomes unavailable for any period of time, this fuels the cloud computing concern of ________.
A. Legacy IT systems B. Privacy C. Reliability D. Security
Computer Science & Information Technology