The __________ Act of 1996 attempts to prevent trade secrets from being illegally shared.
Fill in the blank(s) with the appropriate word(s).
Economic Espionage
You might also like to view...
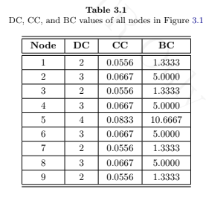
For the networks given in Figures 3.1 and 3.5 of this solution manual, and for an unweighted eight-node path graph, estimate the LInE metric.
Buffer overflow is a condition common to structured programming languages such as the "C" language.
Answer the following statement true (T) or false (F)
In a virtual private network (VPN), a process called _________ is used to carry the data over the Internet; special encryption technology is used to protect the data so it cannot be understood if it is intercepted during transit. A. tunneling B. bridging C. coupling D. linking
Fill in the blank(s) with the appropriate word(s).
The file 76-drill1main refers to the data source for 76-drill1.
Answer the following statement true (T) or false (F)