Describe the inter-mail server vulnerability.
What will be an ideal response?
All e-mail servers communicate with each other using SMTP. However, by the nature of the protocol, there is no reliable way to know when an e-mail message will actually be delivered to a recipient. The primary and/or secondary server might be down, and the message may sit in queues in any number of servers for any amount of time before delivery. E-mail messages are stored in plain, unencrypted text on SMTP servers. Any person who has appropriate access to a SMTP server can read e-mail messages. SMTP servers also communicate with each other in plaintext; thus, any eavesdropper on the network can potentially sniff out e-mail message content. Furthermore, an SMTP server can be configured to request user names and passwords to authenticate in order to relay messages to other servers. These user names and passwords are also sent in plaintext and are subject to eavesdropping.
You might also like to view...
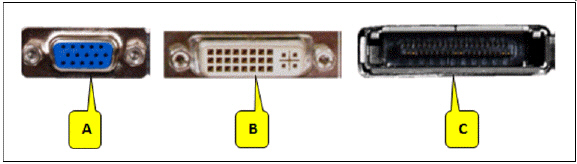 Referring to the accompanying figure, which port is pointed to by callout B?
Referring to the accompanying figure, which port is pointed to by callout B?
A. VGA B. DVI C. HDMI D. USB
What is the master method used for?
a. To solve recurrences b. To optimize recursion c. To compute the Big-O d. To find the recursive base case
Old computer code that is still in use is known as ____.
A. legacy code B. spaghetti code C. Y2K code D. portable code
Which of the following SELECT statements will select the ProdNum field from the tblProducts table, and then sort the records in descending order by the Price field?
A. SELECT ProdNum FROM tblProductsSORT Price DESC B. SELECT ProdNum FROM tblProductsORDER BY Price DESC C. SELECT ProdNum FROM tblProductsWHERE Price DESC D. SELECT ProdNum FROM tblProductsORDER BY ProdNum DESC