In ________ encryption, a key pair is created, where one key is for coding and the other is for decoding
Fill in the blank(s) with correct word
public-key
You might also like to view...
Answer the following statements true (T) or false (F)
1. A Trojan horse is an apparently useful program containing hidden code that, when invoked, performs some harmful function. 2. Packet sniffers are mostly used to retrieve sensitive information like usernames and passwords. 3. A bot propagates itself and activates itself, whereas a worm is initially controlled from some central facility. 4. Every bot has a distinct IP address. 5. DDoS attacks make computer systems inaccessible by flooding servers with useless traffic so that legitimate users can no longer gain access to those resources.
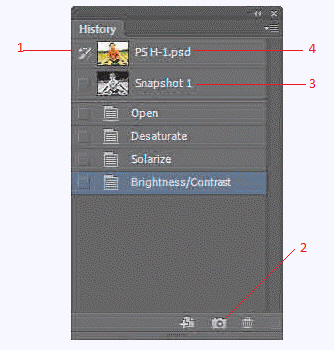 In the accompanying figure, which number represents the Create new snapshot button?
In the accompanying figure, which number represents the Create new snapshot button?
A. 1 B. 2 C. 3 D. 4
In most cases, text that is in columns should be ________
A) left-aligned B) centered C) justified D) right-aligned
One of the vulnerabilities the Morris worm used was a networking service called finger. The purpose of the finger service is to:
What will be an ideal response?