Your company is implementing a wireless network and is concerned that someone from a competing company could stand outside the building and collect wireless data. You have assured the company that WPA2 is secure.
What makes WPA2 more secure than WPA?
A. AES
B. TKIP
C. RADIUS
D. TACACS
Answer: A
You might also like to view...
Which of the following typically is not part of a process’s execution context?
a) general-purpose registers that store process data b) process management registers c) pointers to the process’s parent and child processes d) registers that store pointers to the process’s address space
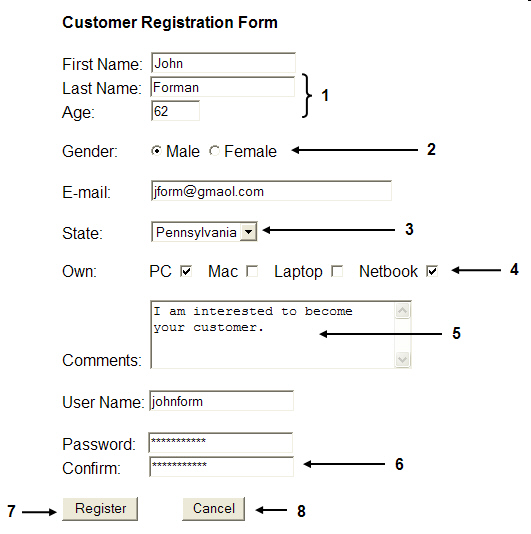 Which numbered item indicates a set of check boxes in the accompanying figure?
Which numbered item indicates a set of check boxes in the accompanying figure?
A. 2 B. 3 C. 4 D. 6
Which of the following lists of phrases uses parallel construction?
A) Turning on the faucet, drinking the water, and turn the faucet off B) She plays volleyball, likes to hike, and runs cross country C) Went running, walking, and then rode her bike D) Mowed the lawn, weeded the flower beds, and put the tools away
Compare an uninterruptible power supply (UPS) with a backup generator.
What will be an ideal response?