________ that describe the purpose of a macro or complex program flows are considered best practice but are many times neglected by database programmers
A) Comments
B) Notes
C) Group
D) Data Actions
A
Computer Science & Information Technology
You might also like to view...
Which of the following String methods does not modify the original String?
a) Method Replace b) Method ToUpper c) Method ToLower d) All of the above
Computer Science & Information Technology
Give two reasons why all the versions of a system based around software diversity may fail in a similar way.
What will be an ideal response?
Computer Science & Information Technology
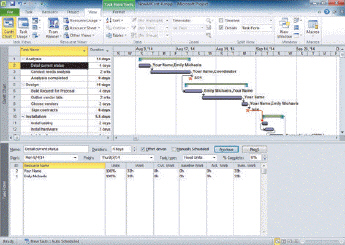 ____ software like that shown in the accompanying figure helps you track and allocate resources.
____ software like that shown in the accompanying figure helps you track and allocate resources.
A. Tax preparation B. Project management C. Personal finance D. Statistical
Computer Science & Information Technology
Which of the following is a hardware or software device that controls traffic and limits specific activity?
a. IDS b. Firewall c. Honeypot d. Honeynet
Computer Science & Information Technology