The ________ button is used to replace each instance of a word found all at once in the Find what field
Fill in the blank(s) with correct word
Replace All
Computer Science & Information Technology
You might also like to view...
In a live acquisition, the investigator has a good idea of what the attacker did to the system during the compromise.
Answer the following statement true (T) or false (F)
Computer Science & Information Technology
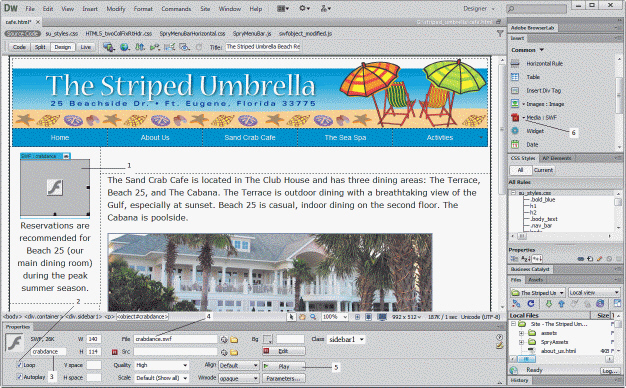 Which item in the accompanying figure refers to the Media button list arrow?
Which item in the accompanying figure refers to the Media button list arrow?
A. 1 B. 2 C. 3 D. 6
Computer Science & Information Technology
Describe an FTP bounce attack.
What will be an ideal response?
Computer Science & Information Technology
The ________ function enables you to review formula results and formulas at the same time.
Fill in the blank(s) with the appropriate word(s).
Computer Science & Information Technology