Specify the value of the data item that could be in the empty node of this 2-3-4 tree.
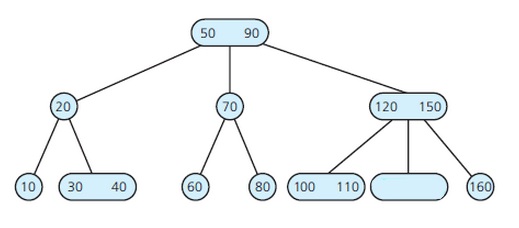
any number between 70 and 90
Computer Science & Information Technology
You might also like to view...
Which of the following statements about buffer overflow attacks is true?
A) Buffer overflow attacks are easy to execute. B) Perfectly written programs are not susceptible to buffer overflow attacks. C) Buffer overflow attacks target systems’ availability. D) Buffer overflow attacks target computer hardware.
Computer Science & Information Technology
To be prepared, test the presentation in the room in which you will make the presentation
Indicate whether the statement is true or false
Computer Science & Information Technology
A macro that executes when an event attached to a control or object occurs is called a(n) ________ macro
Fill in the blank(s) with correct word
Computer Science & Information Technology
Web content that is placed on the desktop is automatically ________ with the Web page
Fill in the blank(s) with correct word
Computer Science & Information Technology