Which of the following best describes an intrusion prevention system?
A) Passive device that analyzes network traffic to detect unauthorized access
B) Active device that sits inline with traffic flow and can respond to intrusions by disabling the connection, dropping the packet, or deleting the malicious content
C) A software or hardware device that can filter incoming or outgoing traffic based on specific rules
D) A device that monitors the characteristics of a single host and the events occurring on that host
B) Active device that sits inline with traffic flow and can respond to intrusions by disabling the connection, dropping the packet, or deleting the malicious content
You might also like to view...
Hypothesize a rationale for the following design decisions:
What will be an ideal response?
______________ are snapshots of a system at a given point of time.
Fill in the blank(s) with the appropriate word(s).
What are the decimal equivalents of the following values (assume positional notation and unsigned integer formats):
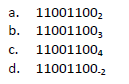
What will be an ideal response?

A. six B. eight C. thirty-four D. twenty-seven