The threat of ____ involves a malicious individual observing another's password by watching the victim while they are performing system login activities.
A. packet monkeys
B. intellectual property
C. shoulder surfing
D. script kiddies
Answer: C
Computer Science & Information Technology
You might also like to view...
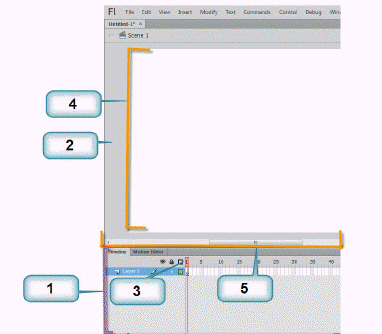 The item marked 4 in the accompanying figure is the ____.
The item marked 4 in the accompanying figure is the ____.
A. Property inspector B. Stage C. Timeline D. pasteboard
Computer Science & Information Technology
A circle that enables you to adjust the height or width of a selected chart.
What will be an ideal response?
Computer Science & Information Technology
Which of the following is not considered one of the five most common business impacts?
a. Financial b. Productivity c. Reputation d. Social e. Safety
Computer Science & Information Technology
CSS stands for _____________________________.
Fill in the blank(s) with the appropriate word(s).
Computer Science & Information Technology