Configuration management systems such as RCS, CVS, and Perforce use file names and their paths to identify configuration items. Explain why this feature prevents the configuration management of CM aggregates, even in the presence of labels.
Note to the instructor: this is a difficult question for students who have not used configuration management systems,
in particular branch management.
The main issue with using path names for identifying configuration items is that path names are attributes of
configuration items and thus, can also change. Assume for example that directories represent subsystems (e.g.,
storage, notification, user interface, train tracking). In the case of a change of the subsystem decomposition, the
directory structure may change (e.g., the storage directory may be split into a database directory and a JDBC
directory). For tools which use path names as identifiers, this translates into configuration items being deleted and
added under a different path name. Since different versions of the same configuration items have different identifiers,
operations such as merging branches are consequently not possible.
You might also like to view...
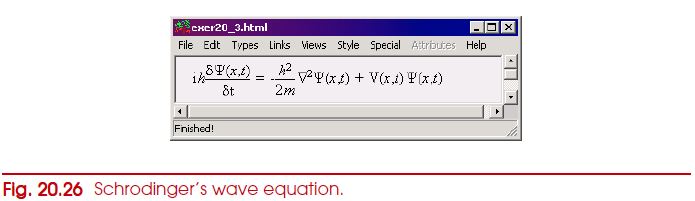
Write a MathML document that represents Schrodinger’s wave equation as shown in Fig. 20.26. [Hint: Symbol psi can be represented by Ψ, and delta by ∇]
When working with co-workers and supervisors, which of the following is a good practice?
A. if you have a problem with a co-worker, first discuss it with other co-workers B. if you need to give bad news or criticism, use email to lessen the blow C. be professional by putting business matters over personal matters D. never tell your boss you can't take on a new project, even if it's beyond your skills
A main advantage of enterprise resource planning (ERP) is that it describes a _____ that ensures connectivity and easy integration of future systems, including in-house software and commercial packages.
A. data frame B. platform C. bandwidth D. hub
If you wanted to process large amounts of scientific data and identify underlying patterns, you would use a _____.
a. supercomputer b. netbook c. minicomputer d. mainframe