What is the name of the protocol that defines a set of common functions that actual authentication methods can use to authenticate users?
A) Expanded Authentication Protocol
B) Wireless Security Protocol
C) Extensible Authentication Protocol
D) Multi-security Protocol
Answer: C) Extensible Authentication Protocol
Computer Science & Information Technology
You might also like to view...
Which Cisco IOS method would be used to configure AAA authentication using a device's user database?
A) local B) login C) database D) username
Computer Science & Information Technology
Promiscuous mode guarantees that the network adapter will capture all the network traffic on the LAN.
Answer the following statement true (T) or false (F)
Computer Science & Information Technology
Name the point(s) that are on the positive x-axis. 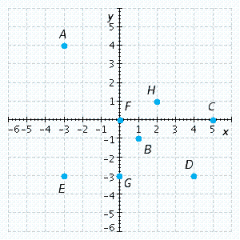
A. D B. F C. C D. A E. E F. H G. G H. B
Computer Science & Information Technology
Which part of a well-designed cryptographic system is responsible for maintaining the secrecy of communications?
a. Identity of sender b. Algorithm c. Key d. Time of use
Computer Science & Information Technology