List and describe two motivations attackers have to attack a network.
What will be an ideal response?
Status-Some attackers attempt to take over computer systems just for the thrill of it. They like to count the number of systems they have accessed as notches on their belt.
Revenge-Disgruntled current or former employees might want to retaliate against an organization for policies or actions they consider wrong. They can sometimes gain entry through an undocumented account (back door) in the system.
Financial gain-Other attackers have financial profit as their goal. Attackers who break into a network can gain access to financial accounts. They can steal individual or corporate credit card numbers and make unauthorized purchases.
Industrial espionage-Proprietary information is often valuable enough that it can be
sold to competing companies or other parties.
You might also like to view...
The companion disk for this text includes a class BuggyCollection. Run the test cases against BuggyCollection to find the bugs in it. Fix the bugs. Remember, you aren’t done until all the tests pass.
What will be an ideal response?
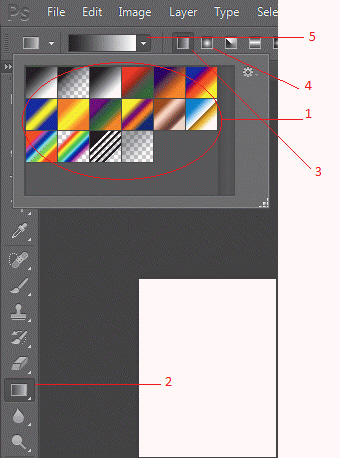 In the accompanying figure, item 1 points to the ____.
In the accompanying figure, item 1 points to the ____.
A. radial gradient B. default gradient swatches C. linear gradient D. gradient tool
 In the accompanying figure, a(n) Revolve effect has been applied to the artwork.
In the accompanying figure, a(n) Revolve effect has been applied to the artwork.
Answer the following statement true (T) or false (F)
What is the difference between using a single-click on the Format Painter and using a double-click?
What will be an ideal response?