The fsck command should only be run on file systems that are in what state?
A. mounted and read/write
B. unmounted or read-only
C. fragmented
D. encrypted
Answer: B
You might also like to view...
Identify the letter of the choice that best matches the phrase or definition.
A. A picture associated with a user name. B. A private combination of letters, numbers, and special characters associated with the user name that allows access to a user's account resources. C. Enables you to sign in to your user account. D. Exits running apps, shuts down Windows, and then turns off the computer. E. A named unit of storage. F. Exits running apps, shuts down Windows, and then restarts Windows. G. A specific named location on a storage medium that contains related files. H. Coordinates all the activities of computer hardware. I. The process of finding a location on a storage device. J. A unique combination of letters or numbers that identifies a specific user in Windows.
Answer the following statements true (T) or false (F)
1. The device management routine that communicates directly with the peripherals is called the input/output control system or IOCS. 2. Primitive I/O commands are sent to an external device by the input/output control system. 3. The only way to read a program or a set of data from disk into memory is to send the drive a series of primitive commands asking it to seek and read the contents of one or more sectors. 4. The input/output control system uses the file system to physically access a disk’s directory. 5. Most utilities are resident.
In SharePoint, ________ enable you to define which document property columns are displayed in a document library
Fill in the blank(s) with correct word
Case 2Andrew is preparing to publish a new Web site using a Web hosting company. He is researching connection types and reviewing the options available in Expression Web.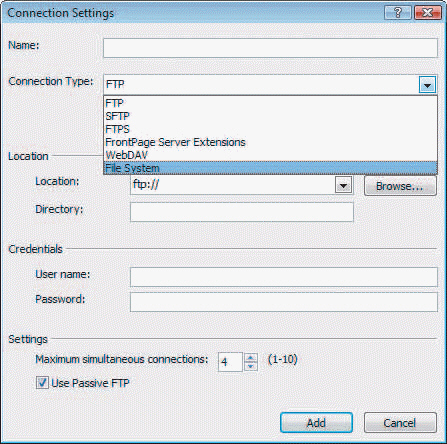 Referring to the figure above, if Andrew chooses to use FTP to transfer files from the source site to the publishing destination, what will he need to know?
Referring to the figure above, if Andrew chooses to use FTP to transfer files from the source site to the publishing destination, what will he need to know?
A. User name and password for his account. B. The address to publish to. C. The file path to the directory in which he plans to publish files. D. All of the above.