?
Critical Thinking Questions
Case 9-2
?
Emily is functioning with her customer, Anna, on the design of a new database. She describes to Anna that key fields are utilized to access, coordinate, and preserve the data records.
?Anna asks if it is manageable to fetch records using a field or combination of fields that is not unique. Emily tells her that it is possible using one type of key. Identify the type of key used here.
A. ?Primary key
B. ?Secondary key
C. ?Foreign key
D. ?Super key
Answer: D
Computer Science & Information Technology
You might also like to view...
The identifiers Vanilla, Strawberry, and Chocolate, which appear inside the braces, are known as ____________.
Look at the following code sample: ``` enum Flavor { Vanilla, Strawberry, Chocolate } ``` a. constants b. references c. mnemonics d. enumerators
Computer Science & Information Technology
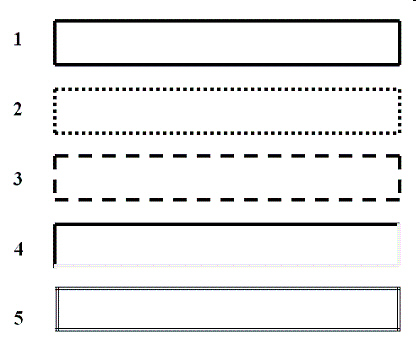 The item marked 3 in the accompanying figure is an example of the ____ style.
The item marked 3 in the accompanying figure is an example of the ____ style.
A. dashed B. groove C. solid D. double
Computer Science & Information Technology
A Cisco switch has four memory areas that store various files as well as the IOS. In which memory area is the bootstrap program stored?
A) NVRAM B) FLASH C) RAM D) ROM
Computer Science & Information Technology
Describe a situation in which you would add comments to a workbook.
What will be an ideal response?
Computer Science & Information Technology