FIGURE 6-2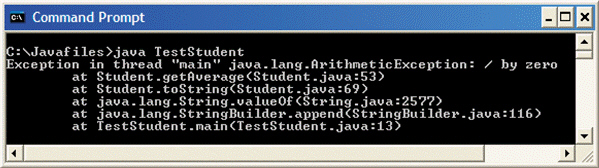 In Figure 6-2 above, the program ____.
In Figure 6-2 above, the program ____.
A. is executing
B. has a run-time error
C. is showing its output
D. is compiling
Answer: B
Computer Science & Information Technology
You might also like to view...
In the Bully algorithm, a recovering process starts an election and will become the new coordinator if it has a higher identifier than the current incumbent. Is this a necessary feature of the algorithm?
What will be an ideal response?
Computer Science & Information Technology
The blank row of a table where new data is entered is called the ________ row
A) paste B) append C) add D) text
Computer Science & Information Technology
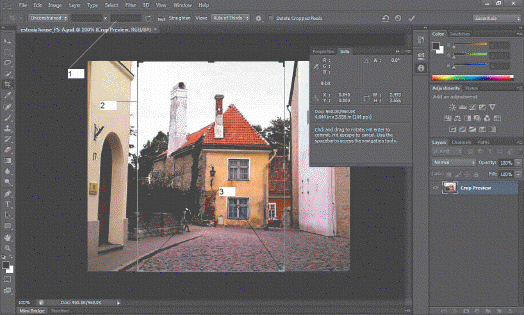 In the accompanying figure, the number 3 refers to the crop handles.
In the accompanying figure, the number 3 refers to the crop handles.
Answer the following statement true (T) or false (F)
Computer Science & Information Technology
The New York Times book blog, ____, often features video interviews with authors whose books are being reviewed.
A. Rocketboom B. Daily Nightly C. Paper Cuts D. iReport
Computer Science & Information Technology