Which of the following utilities performs sophisticated vulnerability scans, and can identify unencrypted data such as credit card numbers?
a. Nmap
b. Nessus
c. Metasploit
d. L0phtcrack
ANSWER: b
Computer Science & Information Technology
You might also like to view...
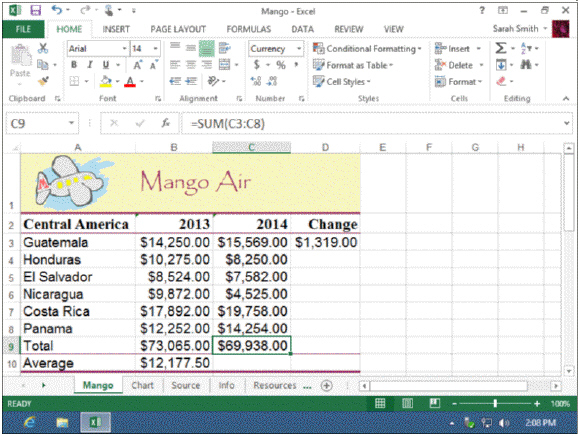 Referring to the accompanying figure, the _____ group contains the button used to paste a formula into a new cell.
Referring to the accompanying figure, the _____ group contains the button used to paste a formula into a new cell.
A. Editing B. Clipboard C. Cells D. Number
Computer Science & Information Technology
The ____________________ tool changes the attributes or properties of a stroke, or it applies a stroke to an object that has no stroke.
Fill in the blank(s) with the appropriate word(s).
Computer Science & Information Technology
Explorer uses a green capacity stripe to indicate drives with more than 10% free space
Indicate whether the statement is true or false
Computer Science & Information Technology
The RS-232 standard specifies that computer devices have ____________________ connectors
Fill in the blank(s) with the appropriate word(s).
Computer Science & Information Technology