Which of the following occurs when a fraudulent buyer submits high bids to discourage other bidders, and then retracts the bids so people they know can get the item at a lower price?
a. Shill bidding
b. Bid shielding
c. Bid siphoning
d. None of the above
Answer B.
You might also like to view...
Terminal Stream operation ________ performs processing on every element in a stream (e.g., display each element).
a. forNext b. for c. forAll d. forEach
Which of the following is the most likely conclusion if a ping message succeeds using an IP address of a host but not the hostname of that host?
A) The problem is associated with DNS. B) The problem is associated with ARP. C) The ACL is not functioning properly in the host. D) The host cannot accept incoming ICMP messages.
Assume that at most 5 tuples in s match each tuple in r.
Compute the cost of 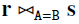 using the following methods:
using the following methods:
(a) Nested loops
(b) Block-nested loops
(c) Index-nested loops with a hash index on B in s. (Do the computation for both clustered and unclustered index.)
where r occupies 2,000 pages, 20 tuples per page, s occupies 5,000 pages, 5 tuples per page, and the amount of main memory available for block-nested loops join is 402 pages.
A text function that combines text strings and inserts a delimiter you specify in the first argument.
What will be an ideal response?