Which of the following authentication protocols sends the password in clear text?
A) PAP
B) SPAP
C) CHAP
D) EAP
A) PAP
Computer Science & Information Technology
You might also like to view...
When picking additional sources you should choose
a. independent sources b. sources created by the same author c. sources with the same domain name d. additional sources are never needed
Computer Science & Information Technology
You can use the Macro Designer to edit existing macros
Indicate whether the statement is true or false
Computer Science & Information Technology
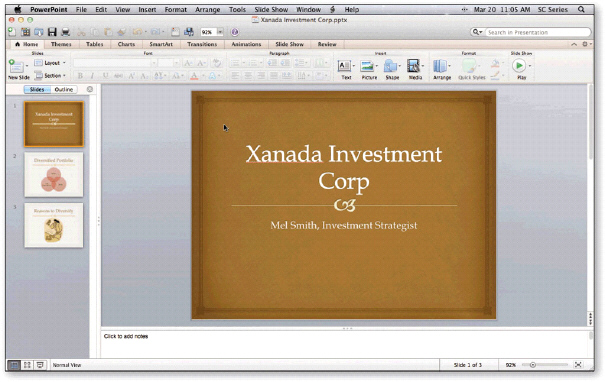 When you create a new presentation, the default ____ layout appears, as shown in the accompanying figure.
When you create a new presentation, the default ____ layout appears, as shown in the accompanying figure.
A. New Slide B. Title Slide C. Blank Slide D. Standard Slide
Computer Science & Information Technology
What are some of the tools used to perform WEP attacks?
What will be an ideal response?
Computer Science & Information Technology