answer the question below:
(a)
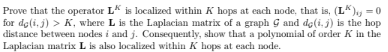
(b)
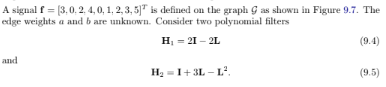
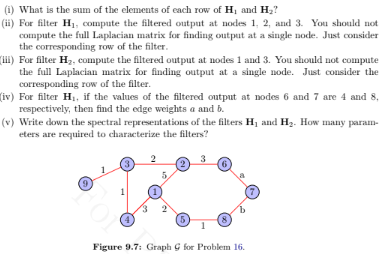


To characterize filter
H2, we need three parameters.
You might also like to view...
Which of the following is an example of a denial-of-service attack?
A) Clicking a link in an e-mail that happens to contain malware B) Installing a keylogger on a system in an attempt to collect usernames and passwords C) Flooding a system with ping requests in an attempt to take it down D) Viewing medical records to satisfy one’s curiosity
?Personalization has little impact on productivity while using a computer.
Answer the following statement true (T) or false (F)
Used to describe deprecated parts of a tag, such as align
A server technician is replacing a web server in an organization. The new server has two integrated NICs. Which of the following describes how the NICs should be configured for fault protection?
A. The NICs should be configured separately with one MAC address. B. The NICs should be placed into a team with one MAC address. C. The NICs should be configured separately with two MAC addresses. D. The NICs should be placed into a team with two MAC addresses.