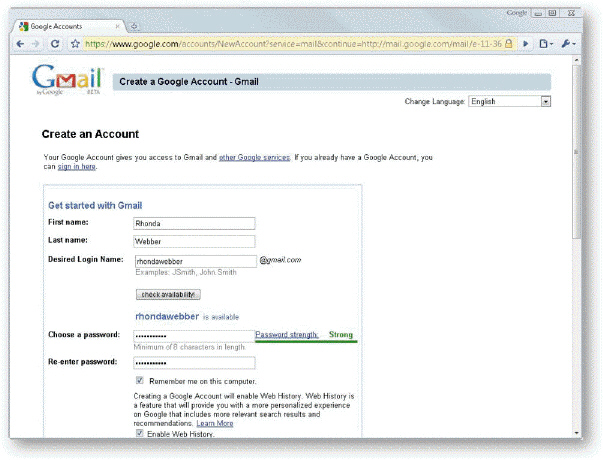
 In the accompanying figure, ____ checks to make sure that the login name you want has not been claimed by another user.
In the accompanying figure, ____ checks to make sure that the login name you want has not been claimed by another user.
A. check availability
B. perform checksum
C. check digit
D. check strength
Answer: A
Computer Science & Information Technology
You might also like to view...
Click SmartArt in the Illustrations group of the ________ tab to select from the SmartArt categories
A) HOME B) DESIGN C) PAGE LAYOUT D) INSERT
Computer Science & Information Technology
"The primary key of a table plays a significant role when setting relationships." Describe why this statement is true
What will be an ideal response?
Computer Science & Information Technology
A formatting specifier code begins with a ____ character.
A. % B. * C. / D. &
Computer Science & Information Technology
To create a link to another file, open the ____________________ dialog box, click Existing File or Web Page in the Link to list, and then click the Browse for File button.
Fill in the blank(s) with the appropriate word(s).
Computer Science & Information Technology