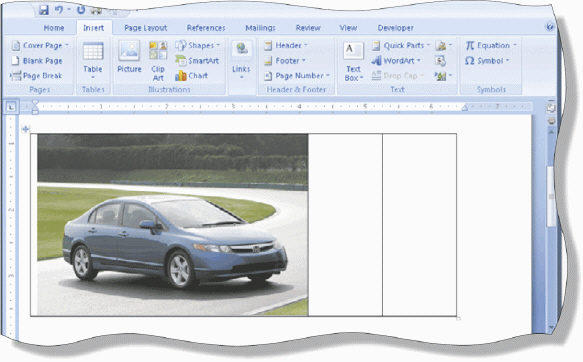
 As shown in the accompanying figure, an image can be displayed in a cell of a table by using a(n) ____________________ object.
As shown in the accompanying figure, an image can be displayed in a cell of a table by using a(n) ____________________ object.
Fill in the blank(s) with the appropriate word(s).
PictureBox
Computer Science & Information Technology
You might also like to view...
A what-if analysis tool used to find a desired value for a cell by changing the value of another cell is called ________
Fill in the blank(s) with the appropriate word(s).
Computer Science & Information Technology
The nearest sensor method can locate a client to within a ____ meter area.
A. 600 B. 670 C. 900 D. 930
Computer Science & Information Technology
Describe the type of data required to create a map in Excel.
What will be an ideal response?
Computer Science & Information Technology
What is the process of discovering design flaws that will open an operating system and its applications to attack or misuse?
A. Vulnerability scoring B. Vulnerability reporting C. Vulnerability research D. Vulnerability assessment
Computer Science & Information Technology