The CompTIA Security+ certification is a vendor-neutral credential.
Answer the following statement true (T) or false (F)
True
You might also like to view...
Answer the following questions with reference to how the ER model in Figure 17.13 maps to relational tables.
The ER diagram in Figure 17.13 shows only entities and primary key attributes. The absence of recognisable named entities or relationships is to emphasize the rule-based nature of the mapping rules described in Step 2.1 of logical database design.
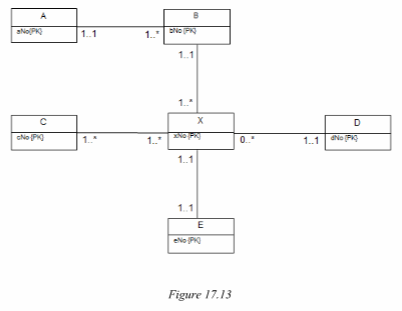
(a) How many relations will represent the ER model?
(b) How many foreign primary keys are mapped to the relation representing X?
(c) Which relation(s) will have no foreign key?
(d) Using only the letter identifier for each entity, provide appropriate names for the relations mapped from the ER model.
(e) If the cardinality for each relationship is changed to one-to-one with total participation for all entities; how many relations would be derived from this version of the ER model?
Network bottlenecks are more common for computers than servers running Windows 10.
Answer the following statement true (T) or false (F)
Based on the dangling-else discussion, modify the following code to produce the output shown. Use proper indentation techniques. You must not make any additional changes other than inserting braces and changing the code’s inden- tation. We’ve eliminated the indentation from the following code to make the problem more chal- lenging. [Note: It’s possible that no modification is necessary.]
``` if (y == 8) if (x == 5) System.out.println("@@@@@"); else System.out.println("#####"); System.out.println("$$$$$"); System.out.println("&&&&&" ``` Assuming that x = 5 and y = 8, the following output is produced:
What happened to the text file? Explain.
Redirect Outputs. a. Use the cd command to change to the /home/analyst/ (~) directory:
[analyst@secOps /]$ cd /home/analyst/ [analyst@secOps ~]$b. Use the echo command to echo a message. Because no output was defined, echo will output to the current terminal window:
analyst@secOps ~]$ echo This is a message echoed to the terminal by echo. This is a message echoed to the terminal by echo.c. Use the > operator to redirect the output of echo to a text file instead of to the screen:
analyst@secOps ~]$ echo This is a message echoed to the terminal by echo. > some_text_file.txtd. Notice that even though the some_text_file.txt file did not exist, it was automatically created to receive the output generated by echo. Use the ls -l command to verify if the file was really created:
[analyst@secOps ~]$ ls –l some_text_file.txt -rw-r--r-- 1 analyst analyst 50 Feb 24 16:11 some_text_file.txte. Use the cat command to display the contents of the some_text_file.txt text file:
[analyst@secOps ~]$ cat some_text_file.txt This is a message echoed to the terminal by echo.f. Use the > operator again to redirect a different echo output of echo to the some_text_file.txt text file:
analyst@secOps ~]$ echo This is a DIFFERENT message, once again echoed to the terminal by echo. > some_text_file.txtg. Once again, use the cat command to display the contents of the some_text_file.txt text file:
[analyst@secOps ~]$ cat some_text_file.txt This is a DIFFERENT message, once again echoed to the terminal by echo.