What are the four typical components of an IDPS?
What will be an ideal response?
Network sensors or host-based agents that analyze and report activity; they are used with management servers that receive and manage information from sensors, analyze data, and identify some events
Detection and prevention capabilities
A command console for interfacing with the IDPS
A database server that stores attack signatures or behaviors an IDPS uses to identify potentially suspicious traffic
You might also like to view...
The _________ delegate represents any method that takes no arguments and returns a result.
a) Func
URL stands for Universal Record Locator
Indicate whether the statement is true or false
Typing a value in a highlighted field while in the ____________________ mode replaces the highlighted field value.
Fill in the blank(s) with the appropriate word(s).
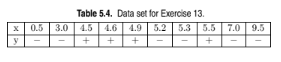
Repeat the previous analysis using the distance-weighted voting ap- proach described in Section 5.2.1.
Consider the one-dimensional data set shown in Table 5.4.