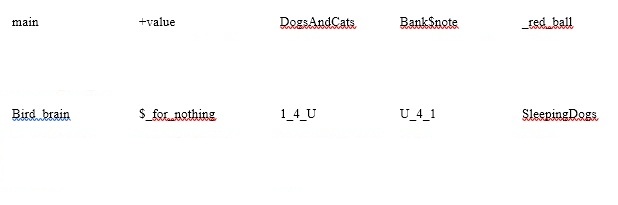
Identify valid variable names for the following, and state why the invalid names are not allowed.

You might also like to view...
To check if a string s contains the suffix "Java", you may write
``` a. if (s.endsWith("Java")) ... b. if (s.lastIndexOf("Java") >= 0) ... c. if (s.substring(s.length() - 4).equals("Java")) ... d. if (s.substring(s.length() - 5).equals("Java")) ... e. if (s.charAt(s.length() - 4) == 'J' && s.charAt(s.length() - 3) == 'a' && s.charAt(s.length() - 2) == 'v' && s.charAt(s.length() - 1) == 'a') ... ```
What are Samba global settings and where are they stored?
What will be an ideal response?
The amount charged to borrow money is called the interest rate
Indicate whether the statement is true or false
_____ usually combines some type of possessed knowledge along with either a possessed object or a biometric feature.
A. ?Two-factor authentication B. ?Mono authentication C. ?Two-factor encryption D. ?Mono encryption