to protect users from each other,3. to protect users from themselves,4. to protect it from itself, and5. to protect itself from its environment.
PTS: 1
2. What are the three security objectives of audit trails? Explain.
What will be an ideal response?
Audit trails support system security objectives in three ways. By detecting unauthorized access to the system, the audit trail protects the system from outsiders trying to breach system controls. By monitoring system performance, changes in the system may be detected. The audit trail can also contribute to reconstructing events such as system failures, security breaches, and processing errors. In addition, the ability to monitor user activity can support increased personal accountability.
PTS: 1
You might also like to view...
Which of the following is not typically part of a process’s address space?
a) text region b) register region c) data region d) stack region
When Internet service providers (ISP) needed a way to create a connection between the customer router and the ISP router that provided a method of authenticating DSL users, what technology was created?
A) PPP B) HDLC C) HDLCoA D) PPPoE
Which of the following is an extension of the fill pattern Sunday, Tuesday?
A. Wednesday, Thursday, Saturday B. Thursday, Saturday, Monday C. Saturday, Sunday, Monday D. Monday, Wednesday, Friday
Solve the system using a graphing calculator. ![]()
A. ![]()
B. 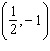
C. ![]()
D. Infinite number of solutions
E. No solution