A ___________ is any process, or a device incorporating such a process, that is designed to detect, prevent, or recover from a security attack. Examples are encryption algorithms, digital signatures and authentication protocols.
Fill in the blank(s) with the appropriate word(s).
security mechanism
Computer Science & Information Technology
You might also like to view...
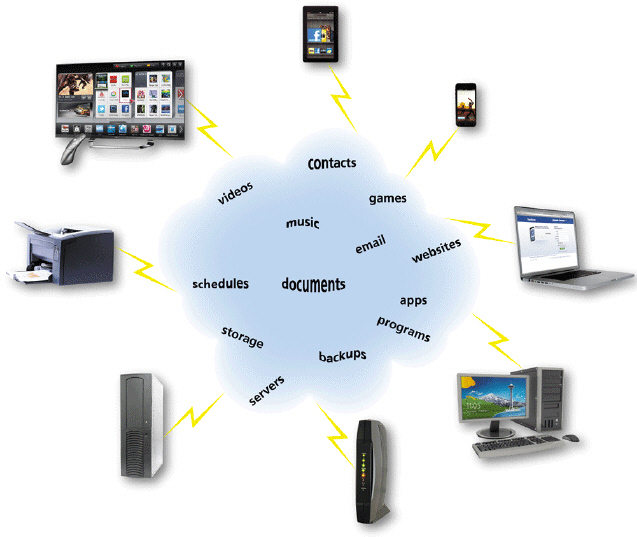 As shown in the accompanying figure, _________________________ refers to a collection of computer servers that house resources users access through the Internet.
As shown in the accompanying figure, _________________________ refers to a collection of computer servers that house resources users access through the Internet.
Fill in the blank(s) with the appropriate word(s).
Computer Science & Information Technology
Which runlevel gives you access to all services, including the GUI?
A. zero B. one C. four D. five
Computer Science & Information Technology
When a table row header is repeated, the row will repeat in this location
a. The first row on following pages b. The last table row c. The second table row
Computer Science & Information Technology
A website template already contains the basic Hypertext Markup Language (HTML) code for the website. Using the template saves time _____.?
A. ?debugging B. ?analyzing C. ?coding D. ?testing
Computer Science & Information Technology