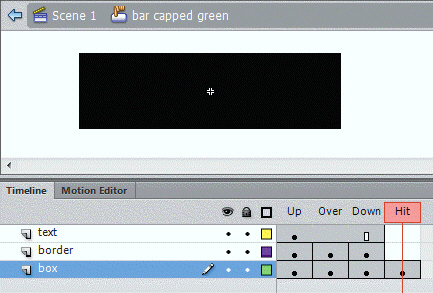
 The large red rectangle featured in the accompanying figure defines the ____________________ area.
The large red rectangle featured in the accompanying figure defines the ____________________ area.
Fill in the blank(s) with the appropriate word(s).
Hit
You might also like to view...
A(n) predefined calculation performs numeric, date, and text computations on each record using data from one or more fields. _________________________
Answer the following statement true (T) or false (F)
The Search option is located on the ________
Fill in the blank(s) with correct word
Which of the following is the most dangerous because it can do more on a computer when it is executed?
A. VBscript B. Active-X C. Javascript D. Java
A user has an Android smartphone that supports full device encryption. However when the user plus into a computer all of the files are immediately accessible. Which of the following should the user do to enforce full device confidentiality should the phone be lost or stolen?
A. Establish a PIN passphrase B. Agree to remote wipe terms C. Generate new media encryption keys D. Download the encryption control app from the store