Which virus detection method creates a virtual environment that simulates the central processing unit (CPU) and memory of the computer?
A. static analysis
B. dynamic scanning
C. code emulation
D. string scanning
Answer: C
You might also like to view...
The format specifier %.2f specifies that two digits of precision should be output ________ in the floating-point number.
a. to the left of the decimal point b. centered c. to the right of the decimal point d. None of the above.
The main internal hard drive on a Windows computer is usually identified as the ________ drive
A) A: B) B: C) C: D) D:
(Odd Numbers Application) The Odd Numbers application should display all of the odd integers from one through the number input by the user. Figure 8.26 displays the correct output for the application. In this exercise, you will use the debugger to find and fix the error(s) in the application.
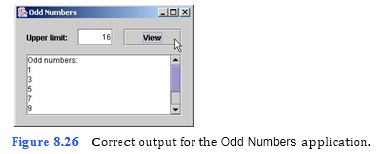
```
a) Copying the template to your working directory. Copy the directory C:Examples Tutorial08ExercisesDebuggerOddNumbers to your C:SimplyJava directory.
b) Opening the Command Prompt window and changing directories. Open the Com- mand Prompt window by selecting Start > Programs > Accessories > Command Prompt. Change to your working directory by typing cd C:SimplyJavaOddNumbers.
c) Running the application. Run the application by typing java OddNumbers. Enter a value into the Upper limit: JTextField, then click the View JButton. Notice that the JButton remains pressed and no output occurs. This is because the application con- tains an infinite loop in the viewJButtonActionPerformed event handler.
d) Closing the running application. Close the running application by clicking in the
Command Prompt window, holding the ctrl key and pressing C.
e) Compiling the application for debugging. Compile the application with the -g com- mand-line option by typing javac -g OddNumbers.j
A forensic investigator might be hired by a prosecutor to determine
A) Whether a company's merger was legal B) Whether a company problem was due to error or fraud C) How healthy a company is before investing in it D) If a company's employees are receiving a fair market wage