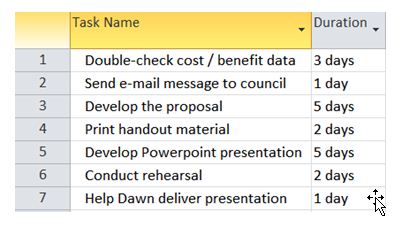
Prepare a list showing all tasks and their durations.
What will be an ideal response?
You might also like to view...
Attack tools can initiate new attacks without any human participation, thus increasing the speed at which systems are attacked.
Answer the following statement true (T) or false (F)
Media files are not searchable.?
Answer the following statement true (T) or false (F)
A security analyst is hardening an authentication server. One of the primary requirements is to ensure there is mutual authentication and delegation. Given these requirements, which of the following technologies should the analyst recommend and configure?
A. LDAP services B. Kerberos services C. NTLM services D. CHAP services
If I have multiple Read Replicas for my master DB Instance and I promote one of them, what happens to the rest of the Read Replicas?
A. The remaining Read Replicas will still replicate from the older master DB Instance B. The remaining Read Replicas will be deleted C. The remaining Read Replicas will be combined to one read replica