__________ are a component of the "security triple."
A. Threats
B. Assets
C. Vulnerabilities
D. All of the above
Answer: D
Computer Science & Information Technology
You might also like to view...
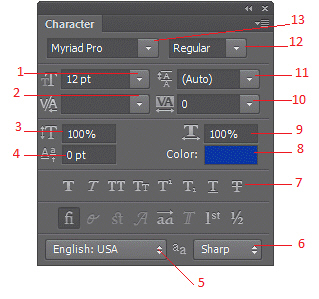 In the accompanying figure, item 3 points to the ____.
In the accompanying figure, item 3 points to the ____.
A. Kerning B. Horizontal scale C. Vertical scale D. Baseline shift
Computer Science & Information Technology
Actions that have been added to buttons are executed when certain scripts occur.
Answer the following statement true (T) or false (F)
Computer Science & Information Technology
A(n) ________ value is character data that usually labels number values located in other cells
Fill in the blank(s) with the appropriate word(s).
Computer Science & Information Technology
WINS is the primary name resolution service in a network involving Windows 7 computers
Indicate whether the statement is true or false
Computer Science & Information Technology