____provide descriptive text for the individual data markers, such as pie slices
A. Asset labels
B. Legend values
C. Data labels
D. Leader lines
Answer: C
Computer Science & Information Technology
You might also like to view...
________ is an ethical system in which conforming to God's law is right, and breaking it is wrong
Fill in the blank(s) with correct word
Computer Science & Information Technology
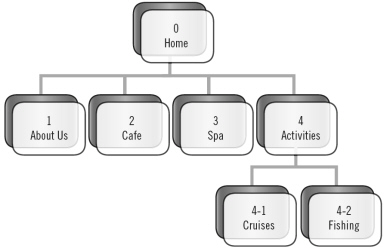 According to the figure above, if you were viewing the home page, how many links to other pages on the site would you find?
According to the figure above, if you were viewing the home page, how many links to other pages on the site would you find?
A. 0 B. 2 C. 4 D. 6
Computer Science & Information Technology
At the Network layer, ____ are used to encapsulate packets (or datagrams).
A. jump rules B. state tables C. bit streams D. frames
Computer Science & Information Technology
Companies can enforce policies for ________.
SSL/TLS IPsec security associations Both SSL/TLS and IPsec security associations Neither SSL/TLS nor IPsec security associations
Computer Science & Information Technology