To select a table, point somewhere in the table and then click the table move handle that appears in the upper-right corner of the table. _________________________
Answer the following statement true (T) or false (F)
False
You might also like to view...
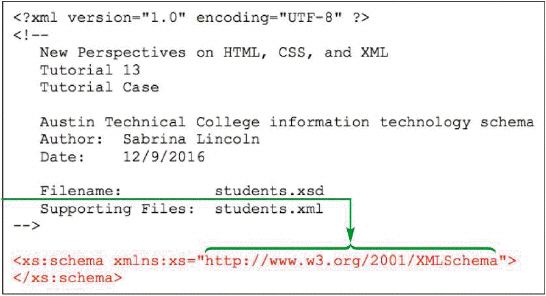 The arrow in the accompanying figure points to the XML Schema ____________________.
The arrow in the accompanying figure points to the XML Schema ____________________.
Fill in the blank(s) with the appropriate word(s).
Which of the following is not a characteristic of an APC?
a) An APC executes in the context of a particular thread. b) An APC can be queued by a kernel-mode component or a user-mode thread with sufficient access rights. c) Kernel APCs are organized in a FIFO queue; however, special kernel APCs are placed at the front of the queue. d) A thread executing an APC cannot be preempted.
To edit a data source during the merge process, click:
a. Address Block b. Edit Data Source c. Edit Recipient List
Default passwords pose unique vulnerabilities because they are widely known among system attackers but are a necessary tool for vendors.
Answer the following statement true (T) or false (F)