____ is the process of using people to get the information you want.
Social engineering
Hacking
Snarfing
Phishing
Social engineering
You might also like to view...
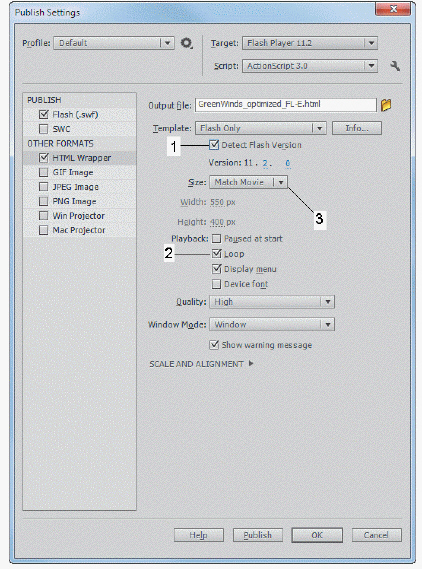 Click the item marked 3 in the accompanying figure to change the size of the Flash movie window in the browser.
Click the item marked 3 in the accompanying figure to change the size of the Flash movie window in the browser.
Answer the following statement true (T) or false (F)
Entering information into grouped worksheets is a very efficient way to simultaneously create page titles and column and row headings in multiple worksheets
Indicate whether the statement is true or false.
If there are seven variables, the ________ value is the 4th variable in the list where there are three variables above and three variables below
Fill in the blank(s) with the appropriate word(s).
Which statement about Multiprotocol Label Switching (MPLS) is true?
A. MPLS is popular because of its ease of use and inexpensive cost. B. MPLS works with any network layer protocol. C. MPLS is dependent on Data Link layer technology. D. MPLS will run over ATM, frame relay, SONET, but not Ethernet.