When creating a public / private key pair, for which of the following ciphers would a user need to specify the key strength?
A. SHA
B. AES
C. DES
D. RSA
Answer: D. RSA
You might also like to view...
Showthat step 3 of the method used in Section 16.3.1 to perform a join using a semi-join does in fact generate the join. For simplicity, assume that the join we are attempting is a natural join. In other words, show that
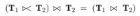
What will be an ideal response?
With respect to organizations, confidentiality means protecting __________ information about company finances, procedures, products, and research that competitors would find valuable.
Fill in the blank(s) with the appropriate word(s).
How can you correct errors in data?
What will be an ideal response?
The most widely used public cryptography system for encrypting e-mail messages on Windows systems is a commercial product called ____________________.
Fill in the blank(s) with the appropriate word(s).