GAD Systems is concerned about the risk of hackers stealing sensitive information stored on a file server. They choose to pursue a risk mitigation strategy. Which one of the following actions would support that strategy?
A. Encrypting the files
B. Deleting the files
C. Purchasing cyber-liability insurance
D. Taking no action
Answer: A. Encrypting the files
Computer Science & Information Technology
You might also like to view...
It's good practice to provide a(n) ____________ when connecting to anonymous FTP sites.
a. password b. email address c. IP address d. host name
Computer Science & Information Technology
When configuring PHP for compiling on Linux or macOS, use the _________ configuration flag.
a. --disable-short-tags b. --enable-libgcc c. --with-gettext d. --with-libdir
Computer Science & Information Technology
When you use the dialog box shown in the accompanying image to change the resolution of an image, Photoshop will ____________________ the image.
Fill in the blank(s) with the appropriate word(s).
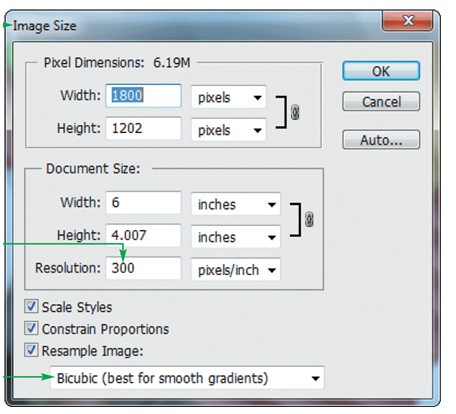
Computer Science & Information Technology
In a PivotChart report, any ________ can be assigned to either axis
A) field B) record C) value D) label
Computer Science & Information Technology