Bugs are normally labeled as ____.
A. programmer mistakes
B. logic errors
C. handled exceptions
D. unhandled exceptions
Answer: A
You might also like to view...
The structure of the EBK makes it easy to add that standard role to the 10 basic roles that are presently contained in the model.
Answer the following statement true (T) or false (F)
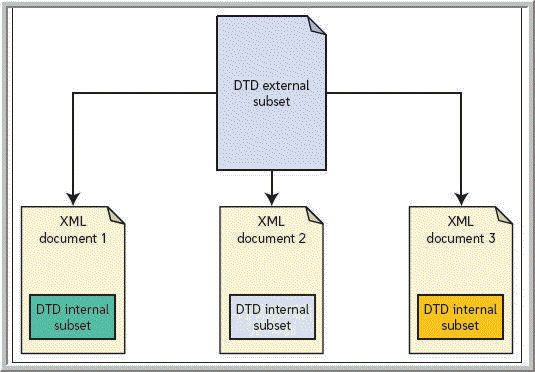 Which of the following is a part into which a DTD like the one in the accompanying figure can be divided?
Which of the following is a part into which a DTD like the one in the accompanying figure can be divided?
A. element declaration B. strict declaration C. external subset D. root element
Case-Based Critical Thinking QuestionsCase 7-2Your roommate knows that you have a lot of expertise with video, so she asks you for a quick primer. Your roommate has a file with an extension she has never seen before, and she doesn't know what it is. You tell her it's for an earlier Microsoft format designation that has largely been replaced by the Windows Media format. What's the name of the file?
A. video.avi B. video.smil C. video.mpg D. video.rm
________ code for the Linux operating system is publicly available
Fill in the blank(s) with correct word