Using the Help feature, determine what security features are available in Visible Analyst®, or another CASE tool. Describe what you found in a brief memo, and include screen shots if possible.
What will be an ideal response?
Visible Analyst describes different security environments for single-user vs. network versions. Here are several screens that explain single-user security:
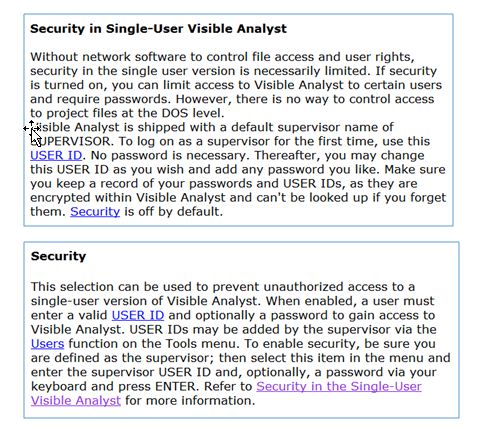
Here is how to turn on the Security feature,
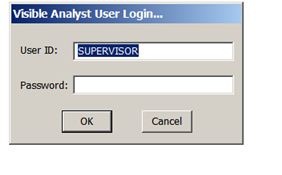
And here is where the Supervisor can add authorized users and groups:
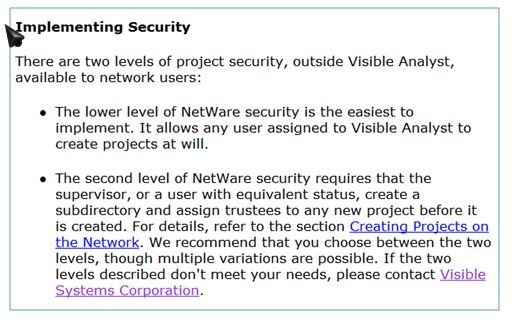
Here is a brief discussion of the network version, which includes typical network security features and methods.
You might also like to view...
Clearing the On Mouse Click option and entering 00:07.00 in the After box located in the Timing group and clicking Apply To All, will cause each slide to advance after being displayed for 7 minutes
Indicate whether the statement is true or false
Match the following views in PowerPoint 2010 with its function:
I. Notes Page view A. deliver a presentation on two monitor simultaneously II. Slide Sorter view B. view one slide at a time with a title bar and Close button III. Slide Show view C. to enter and edit large amounts of text for the speaker to refer to IV. Reading view D. view multiple slide at one time V. Presenter view E. deliver the final presentation to an audience
________ graphics are designer-quality visual representations of your information that you can create by choosing from the many different layouts to communicate your message or ideas effectively
Fill in the blank(s) with correct word
Document properties, such as the name of the file and the author of the document, are also known as ________
Fill in the blank(s) with correct word