The scrambling code used to attempt to modify a(n) _______________ virus to prevent detection is actually used as the signature to detect the virus.
Fill in the blank(s) with the appropriate word(s).
polymorph
correct
Computer Science & Information Technology
You might also like to view...
Which programming language is typically used for Android development?
a. C b. Java c. Python d. C# e. Perl
Computer Science & Information Technology
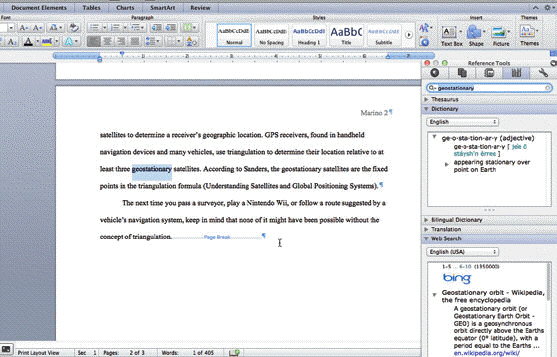 You can use the Copy and Paste commands to copy information from the Reference Tools pane into your document, as shown in the accompanying figure.
You can use the Copy and Paste commands to copy information from the Reference Tools pane into your document, as shown in the accompanying figure.
Answer the following statement true (T) or false (F)
Computer Science & Information Technology
Reports based on parameter queries display the same subset of data each time it is run
Indicate whether the statement is true or false
Computer Science & Information Technology
Most UTP cables come with stranded __________________ fibers to add strength to the cable.
Fill in the blank(s) with the appropriate word(s).
Computer Science & Information Technology