Some programmers prefer not to use protected access because they believe it breaks the encapsulation of the base class. Discuss the relative merits of using protected access vs. using private access in base classes.
What will be an ideal response?
private data members are hidden in the base class and are accessible only through the public or protected member functions of the base class. Using protected access enables the derived class to manipulate the protected members without using the access functions of the base class. If the base-class members are private, the member functions of the base class must be used to access the data. This may result in a decrease in performance due to the extra function calls, yet accessing and modifying private data in this indirect manner helps ensure that the data in the base class remains consistent.
You might also like to view...
Modify any of the methods from the last chapter to use a nested loop. Run it to make sure it still works.
What will be an ideal response?
In a query, you can group the data by the values within one of the columns. ?
Answer the following statement true (T) or false (F)
?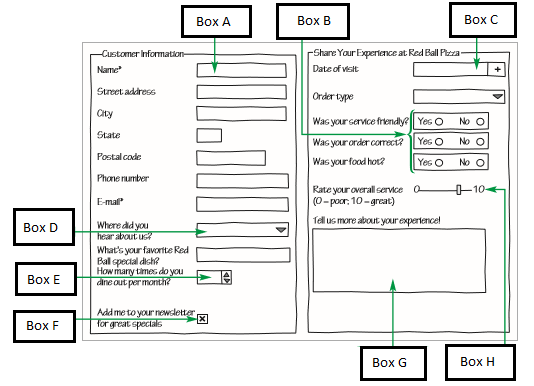
A. ?slider control B. ?spin box C. ?calendar control D. ?check box
________ techniques include creating viruses and worms, performing denial-of-service (DoS) attacks as well as establishing unauthorized remote access connections to a device using Trojans/backdoors, creating botnets, packet sniffing, phishing, and password cracking.
A. Personal-hacking B. Network-hacking C. Server-hacking D. Intelligence-hacking