When you first save a document, the default filename of the file is based on the first few words of the document.
Answer the following statement true (T) or false (F)
True
You might also like to view...
What changes appear in the window after starting the Routing and Remote Access service?
Starting and Stopping the Routing and Remote Access Service
a. Click Start > Search and select Control Panel > Click Network and Sharing Center.
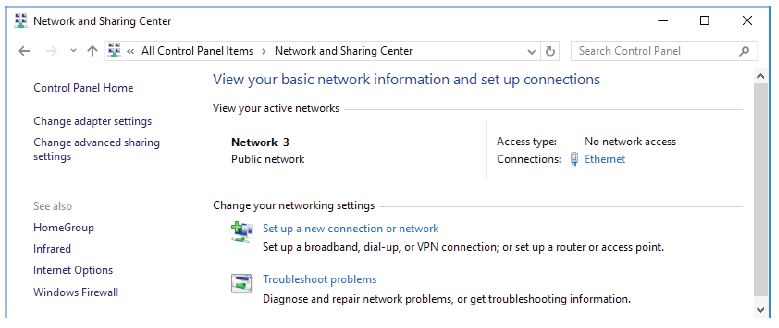
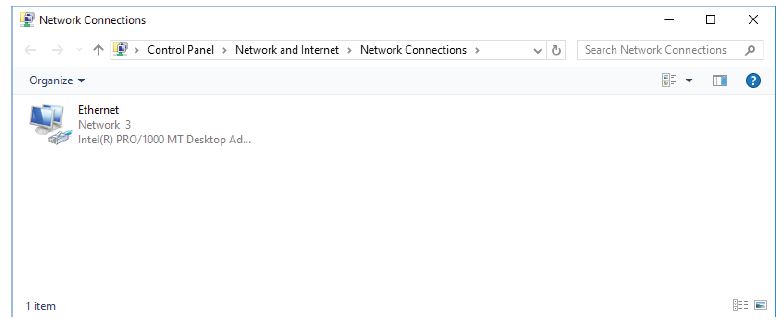
b. Click Change adapter settings in the left pane. Reduce the size of the Network Connections window and leave it open.
c. Navigate to the Administrative Tools. (Click Start > Search for and select Control Panel > Click Administrative Tools)
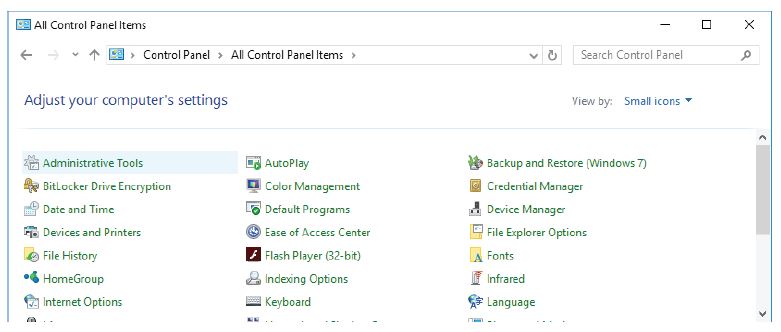
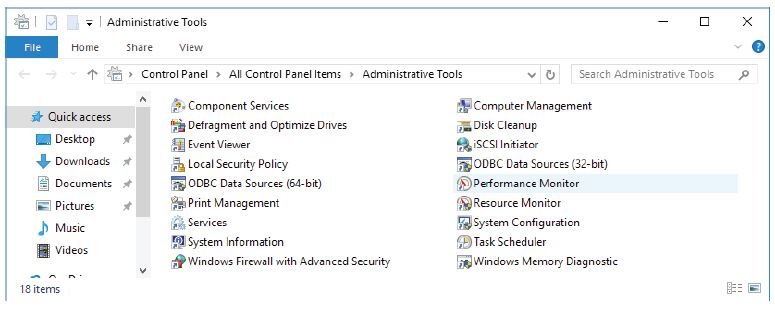
d. The Administrative Tools window opens. Double-click the Performance Monitor icon.
e. The Performance Monitor window opens. Make sure Performance Monitor in the left pane is highlighted. Click the Freeze Display icon (pause button) to stop the recording.
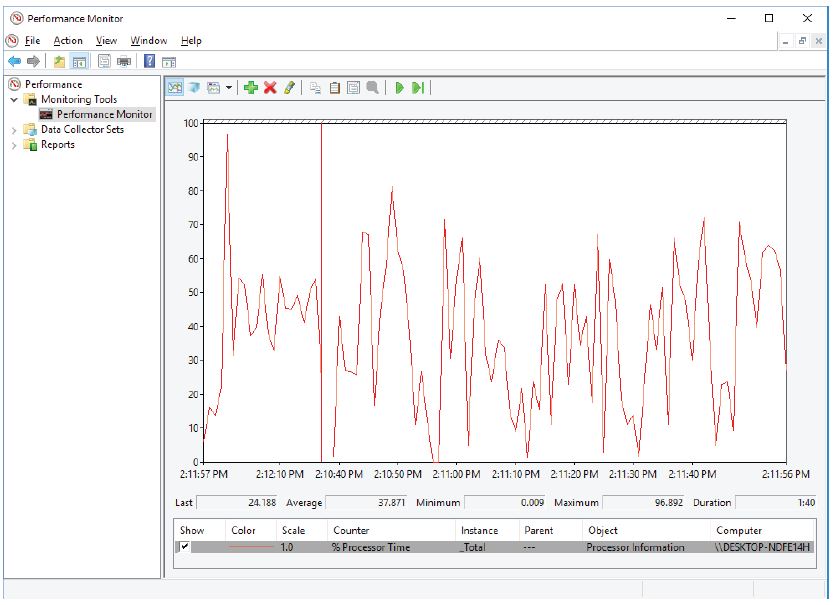
f. Right-click the Performance Monitor menu bar and select Clear to clear the graph. Leave this window open.

g. Navigate to the Administrative Tools window and select Services.
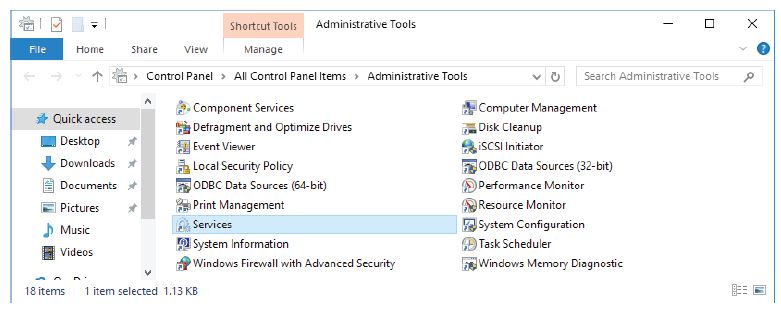
h. Expand the width of the Services window so you have a clear view of the content. Scroll down in the right pane until you see the service Routing and Remote Access. Double-click Routing and Remote Access.
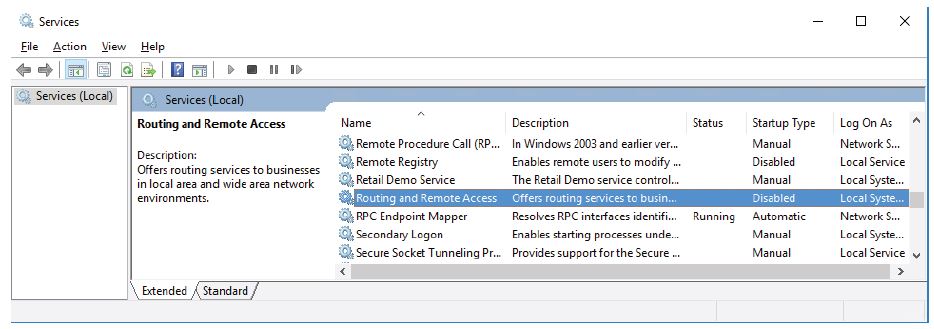
i. The Routing and Remote Access Properties (Local Computer) window opens. In the Startup type drop-down field, select Manual and then click Apply. The Start button is now active. Do NOT click the Start button yet. Leave this window open.
j. Navigate to the Performance Monitor window. Click the Unfreeze Display icon to start the recording.
k. Click the Routing and Remote Access Properties (Local Computer) window. To start the service, click Start. A window with a progress bar opens.
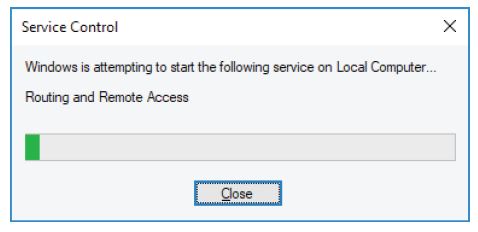
l. The Routing and Remote Access Properties (Local Computer) window now shows the Stop and Pause button active. Leave this window open
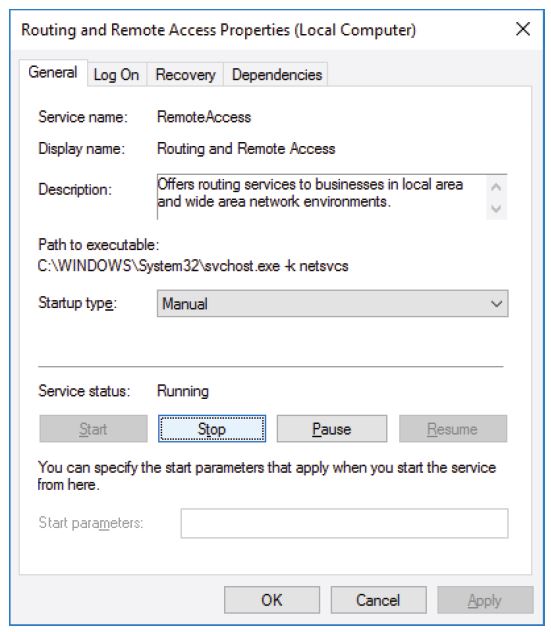
m. Navigate to the Network Connections window. Press the function key F5 to refresh the content.
Which of the following is not a firewall technology?
a. Packet filtering. b. Proxy server. c. Stateful packet filtering. d. All the above are firewall technologies.
What is a block cipher algorithm that operates on 64-bit blocks and can have a key length from 32 to 448 bits?
A. Twofish B. Blowfish C. Whirlpool D. Rijndal
In general, SQL is case-sensitive.
Answer the following statement true (T) or false (F)