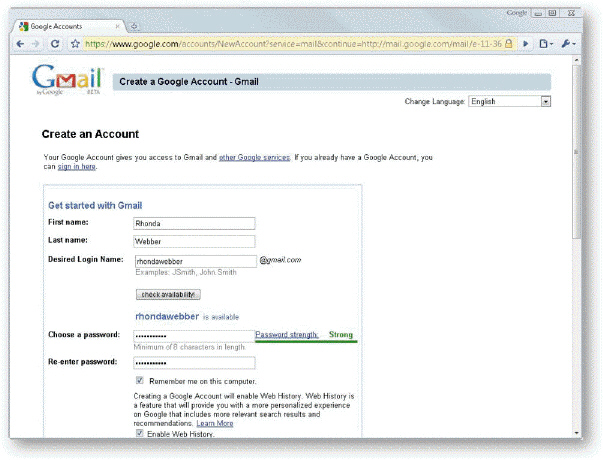
 In the accompanying figure, ____________________ indicates that the user's chosen password contains a mix of letters, numbers, and keyboard symbols.
In the accompanying figure, ____________________ indicates that the user's chosen password contains a mix of letters, numbers, and keyboard symbols.
Fill in the blank(s) with the appropriate word(s).
strong
You might also like to view...
Which of the following statements is true?
a. The binary search algorithm is less efficient than the linear search, but it requires that the array be sorted. b. The binary search algorithm is more efficient than the linear search, but it requires that the array be unsorted. c. The binary search algorithm is more efficient than the linear search, but it requires that the array be sorted. d. The binary search algorithm is less efficient than the linear search, but it requires that the array be unsorted.
A list that uses shapes and symbols is called a ________ list
A) bulleted B) numbered C) random D) styles
List three ways an inverter can cause damage to a technician or the component itself.
What will be an ideal response?
Why is the hit rate of an L2 cache usually lower than that of an L1 cache?
What will be an ideal response?